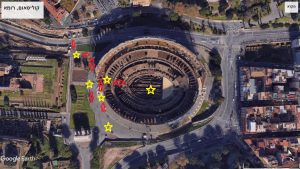
Summary of event details as published in the media:
Stephan Balliet, a 27-year-old German extreme right-winger, was traveling in a rented vehicle in front of a synagogue in Halle on Humboldtstraße on October 9 at noon. He aired his actions live on the streaming Twitch platform, explaining his actions, in German and English. During his remarks, he denied the Holocaust, expressed anti-Semitic attitudes to Jews and foreigners and expressed himself against feminism. Later in the documentation, it can be seen that he had additional rifles, ammunition, explosives and Molotov cocktails in the vehicle. Police searches of the vehicle found four pounds of explosives.
The event began at around 1:15 pm on Yom Kippur 2019 when between 70 and 80 members of the Jewish community prayed in the synagogue. The gunman fired several shots at the synagogue door, and he even used an explosive device, but he failed to enter the synagogue. He tried to enter the synagogue through three entrances; All three were closed. He failed to shoot a submachine gun at a passerby in the street next to the synagogue, and also at the tire of the bystander’s vehicle. As another bystander approached, he tried to shoot at him as well, but the weapon he used had a stoppage that because of this the bystander was able to evade. According to other reports, the gunman threw a grenade at the nearby Jewish cemetery in Halle.
Due to his failure to enter the synagogue, he drove his car to Schillerstraße, stopping at the kebab restaurant on Ludwig-Wucherer-Straße. First, he tried to throw explosives at the fast-food restaurant, but the material got stuck in the restaurant door and exploded in the street. Then he shot at the diners in the restaurant, until the arrival of the security forces. He later fled toward the exit from the city; On his way, he stopped in the garage and demanded those present with threats and shootings a new vehicle. The suspect in the attack was arrested by the police near a construction site on Federal Highway 91 after causing an accident.
The attempt at the attack is no less than a formative event of all Jewish communities throughout the world, an event that, on the one hand, shows the reality of racism against Jews that repeatedly produces individual perpetrators and on the other, proves that awareness of threats and proper professional preparation provide a life-saving response.
The fact that the German terrorist failed to enter the synagogue is an unequivocal result that combines emergency preparedness, threat identification and correct response from the synagogue’s rabbi, security guard, and worshipers and is not at all related to luck or chance.
The perpetrator
Recent terrorist attacks against Jewish communities around the world have set an alarming reality in which racism against Jews raises its head in the form of individual perpetrators who are motivated by strong hatred, which is mainly circulated online through racist articles and violent computer games that contain overt or hidden messages against strangers.
Stephan Balliet fits the profile of a single perpetrator that has formed an extreme opinion against foreigners in his country and has apparently decided on his own to massacre with the aim of killing as many Jews as possible by weapons and explosives and to produce a media wave for his actions that will cause more and more copycat attacks.

In the picture is Stephan Balliet, whose likeness shows the characteristics of the contemporary perpetrators, the hatred is seen in their faces, who are ready to die in order to kill foreigners and especially Jews in cold blood, who imitate other perpetrators, who learn how to obtain and / or manufacture weapons, who dress and behave like murderous characters from computer games and who expect to have a murderous revolution in their country in particular and in the world in particular.
In today’s reality, our world is full of these kinds of perpetrators who just go out one day to do the fatal sometimes unannounced action and sometimes write a Facebook post describing their intentions and post it shortly before they carry out the attack.
Stephan’s picture dressed as a fighting character from a computer game:

The readiness and ability to cope with a single perpetrator
In recent years, security forces all over the world have been using numerous resources to create an intellectual circle that tries to detect in advance individual attacks like Stephan Balliet. Certainly, the intelligence effort manages to identify some of these attacks in time, but there is no chance that they will do so at a success rate of a 100 percent, which means there will always be a single attacker that will not be identified in time and thus they carry out their plans.
Coping with these kinds of perpetrators starts with awareness of the problem and the real threat, continuing to carry out network preventive actions and ending in the ability to thwart attacks. The thwarting phase is the most difficult because it occurs after the perpetrator has already started his malicious and fatal action. Precisely because the security forces start responding when the perpetrator is already operating, they are required to have a level of readiness and the highest professional level possible. Once the perpetrator is identified, whether, by citizens or security personnel, the response should be swift, determined and accurate. Any delay in responding gives the perpetrator extra time to put more and more innocent civilians at risk.
In Israel, unlike most European cities, many civilians are aware of the danger of the attacks when some are even armed with a personal firearm, security personnel (police and soldiers) stay at home and during their free time with weapons and many areas are manned by police and soldiers, which increases the likelihood of identification of the attack as well as the response happens a short time after the beginning of the attack, preventing the worsening of the situation.
According to reports in the German media, Stephan Balliet was caught an hour and a half from the time he began the attempt to enter the synagogue in Halle. This is undoubtedly a time period that makes no sense and is inconsistent with what is expected from skilled security forces. Allowing a cruel perpetrator to move about an hour and a half undisturbed with many weapons and explosives indicates that local security forces are not prepared to deal with such emergencies.
Video about the attack posted in the local media:
Inspirationally and encouragingly, the Jewish community led by the rabbi of the synagogue who stayed for Yom Kippur prayers were aware and prepared and therefore responded in a way that saved their lives. The readiness of the community is manifested in the armoring of the synagogue, the identification of the threat and the prompt and effective response. Documentation of the attacker’s attempts to break through the main entrance door to the synagogue complex and other secondary doors prove what I have written in previous event analyses, that the main entry area and especially the front door is the first and main obstacle that can impede the attacker and even prevent him from entering, thus giving the citizens time to evacuate, fortify or prepare for a counter-attack.
Documentation of Stephan Balliet attempting to break through the main entrance to the synagogue:
Picture of the door after the shooting:

The synagogue rabbi said at the end of the event that during the Yom Kippur prayer there were about 70 worshipers when the security guard suddenly recognized the threat from the outside and thus started the response, locking the front door and the secondary doors, evacuating everyone in the synagogue on the first floor and leaving a reaction force in case the perpetrator breaks through one of the doors and steps inside. As previously mentioned, the synagogue’s doors were not broken into or opened, causing the victim to get frustrated and start looking for unsuspecting victims in the street.
The awareness, preparedness, identification and response of the synagogue rabbi, the security guard and the worshipers what saved their lives. I have no doubt that they attended lectures and underwent training that has prepared them for these kinds of emergencies.
Sometimes the best defense is the attack
During his search for other foreign victims, Stephan Balliet documented how he entered a Turkish restaurant and shot at persons at the scene:
The video shows the different choices of response by the citizens in the restaurant from the moment they realize that an attacker with a weapon has been entered into it in order to murder them in cold blood. Some of the citizens chose to escape to the back room and may have stepped out of the restaurant and some chose to hide behind the drink machine. The civilians hide while a perpetrator fails to manipulate the weapons in his hand and shoot at them. During this time given to them, the civilians remain in a shelter in the hope that the perpetrator will not be able to shoot them and even begin to cry and beg for mercy for their lives. I do not judge the civilians and yet think that in such a situation it is better to go on the attack because the defense is simply ineffective because it leaves you 100 percent exposed to the real and imminent threat.
This difficult situation illustrates the importance of taking action to raise awareness among citizens of this kind of growing danger and the need to acquire skills in contact to improve self-confidence and the ability to respond in emergencies. Krav maga training improves the ability to react against the natural instinct of escape and hiding.
Individual attackers have become part of the most and more realities in the world, so it is imperative for everyone, security forces and civilians to work to raise awareness of the threat, to protect sensitive facilities, to improve identification and to acquire skills and tools for a fast, determined and effective response.