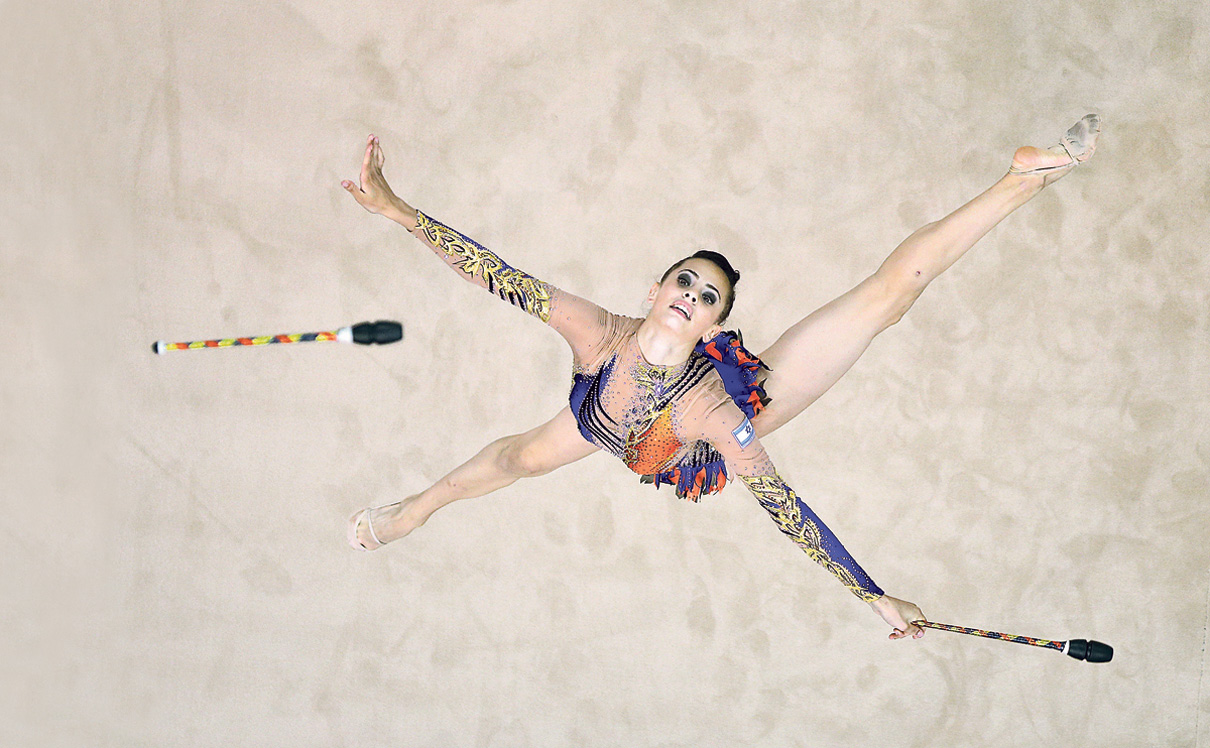Article author: Miky Weinberg – Owner of the Tarantula Technologies Ltd and Octagon Security Ltd Companies.
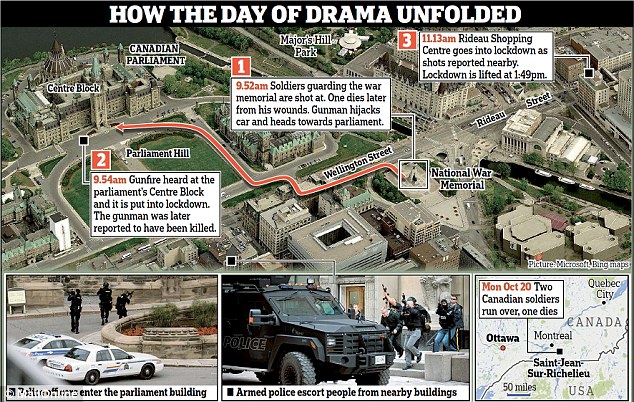
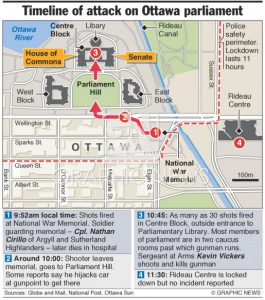
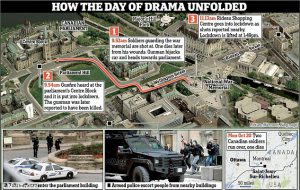
April 30, 2003, at almost 01:00, a loud explosion tears apart the Tel Aviv nightlife and dismantles the opening of the Mike’s Place nightclub at the height of a lively and entertaining night party. Dozens of wounded, dead, police and ambulances, crowds, and fear of death that gripped the survivors of the explosion and paralyzed them to silence mixed with helpless looks in front of the tragic sights and the pungent smell that burned in the nose and memory for many years to come.
Moments before, Avi Tabib, the club’s regular security guard, meets in his eyes a man who seems unusual in his behavior, Avi, with a hunter’s instinct who has adapted himself thanks to his street smarts, felt something he could not ignore about the approaching person. Avi reciprocates in his heart that this is a person who will cause problems at the club and therefore makes a decision not to let him in. From here it all happens at breakneck speed:
Their eyes cross, the unusual person reaches the entrance to the club and stands in front of Avi.
The guy probably understands he’ll have a problem with the security guard. Avi is determined to stop him and not allow him to enter the club. Avi addresses him verbally, and the guy replies in English that he wants to go into the club to drink beer. Avi explains that he cannot enter the club tonight. The unusual person moves a few steps back, Avi turns to talk to one of the employees standing next to him, the unusual person tries to take advantage of this and progresses to the entrance with a quick walk and tries to go between Avi and the employee, Avi makes physical contact to stop his progress and prevent him from entering, Avi places his two hands on the unusual man’s waist and pushed him back without any special resistance on his part, suddenly Avi feels a change in the guy’s behavior, his body as if slightly tensed. Avi the security guard is trying to figure out what the matter is.
At that moment, a violent explosion ripped through the night on the promenade in Tel Aviv, total destruction within a few tens of meters, people flew in all directions, the terrorist’s body was split in two, and Avi the security guard, who was closest to the center of the explosion flew a huge distance and he hit his head on one of the club tables.
Avi is lying on the floor, his body was the first to absorb the force of the explosive device that pierced the heart of Tel Aviv and the news channels throughout the country.
“Avi Tabib, the permanent security guard of Mike’s Place, is dead” – this is what everyone who knew him and stayed at the club at the time of the attack thought and said. No one believed that there was a person who could absorb such an explosion and stay alive.
Avi, the security guard, they thought to themselves- Avi prevented the suicide bomber from entering the club and with his body saved many other people.

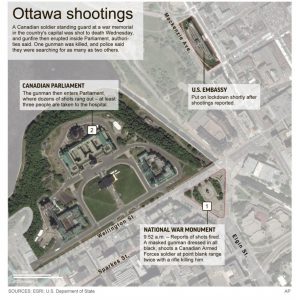
The attack on Mike’s Place club on April 30, 2003, was a suicide bombing carried out by two British British Muslims of Pakistani origin at the entrance to the club at the Herbert Samuel 86 platform in Tel Aviv. A first terrorist blew himself up at the entrance after Avi the security guard prevented him from entering and the second fled the scene. Three people were killed in the attack and more than 50 were injured. The terrorist organizations Hamas and the al-Aqsa Martyrs Brigades claimed joint responsibility for the attack. A Hamas video was later released in the Gaza Strip of the terrorists in uniform and weapons under the Hamas flag.

The attack was planned as a qualitative attack and a mass attack and was carried out against the background of the publication of the “Road Map” plan – to end the Israeli-Palestinian conflict. A plan was presented by US President George W. Bush in his speech on June 24, 2002.
The choice of Mike’s Place was due to a number of reasons: both because of its location – in the neighborhood of the United States Embassy, both because of the large number of foreign citizens in it, and because it is popular and crowded with people.
The intention was to use two suicide bombers of British descent with standard plastic explosives. The use of foreign nationals is intended to increase difficulties in the Israeli security mechanisms in detecting the terrorist team. The use of two terrorists was to increase the number of casualties and the use of standard plastic explosives to make it difficult to detect and signal the capabilities of the sending organization.
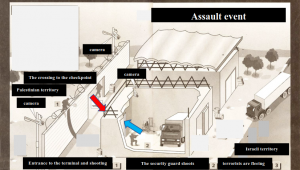
On the day of the incident at 00:45, Asif Muhammad Hanif and Omar Khan Sharif, two British suicide bombers of Pakistani origin, arrived at the club. Asif Muhammad Hanif tried to enter the club but aroused the suspicion of Avi Tabib the security guard who refused to let him into the club. After a brief argument in which the terrorist realized that the security guard insisted on not entering, he moved a little to the side to calculate his steps, when at the same time the late Dominic Hess who worked at the place went to talk to Avi the security guard. The terrorist who thought Avi the security guard was not watching tried to break into the club. Avi the security guard blocked the terrorist’s path and pushed him from the front door towards the road. During the fight outside the club, he blew himself up on Avi the security guard.
I know I’m going to surprise you, Avi the security guard, the one who absorbed the full energy of the explosive device detonated by the terrorist, survived, and was evacuated to the hospital in a very critical condition. The doctors fought for his life with all their might and allowed him to get his life back. Avi’s speedy recovery was defined as a medical miracle. And for him to stand in front of me now and tell me his unbelievable story, now all we have left to do is learn from whoever was there.
Today, September 14, 2020, I met with Avi Tabib the legendary security guard of the Mike’s Place club to hear and learn from him about the event as a firsthand source.

Thanks to his special character, sharp senses, street smarts, courage, and strong body, Avi Tabib saved the lives of many other people, and today he met with me to describe the evening of the attack and no less important the process that went through the evening of the attack out of understanding the importance of conveying professional lessons and messages to everyone who deals with the security profession and especially for those who take part in civil security.
Hello Avi, I am so happy to meet you and get to know you and your unique and instructive personal story.
Avi Tabib: Thank you. I think what you are doing is nothing less than a mission that will undoubtedly help many security guards to better understand the essence and importance of the role of the security guard wherever he is. Over the years, since the attack, I make sure to give lectures to security guards to explain to them that being a security guard is not a summer camp and further on that, I think an article on your blog will add value to this mission.
What is your background, how did you get into security?
Avi Tabib: Just by chance. After military service, I flew to the United States and stayed there for ten years. During these years I studied martial arts and at some point, I started working as a security guard at one of the clubs. The skills I acquired in combat and the work experience raised my self-confidence and sense of ability. Over time I felt all the time that I knew what I was doing.
When did you return to Israel and start working at Mike’s Place?
Avi Tabib: A month after the events of 9/11 in the United States, I returned to Israel. I began to reorganize – studies and work. At the same time, Operation Defensive Shield began in Israel and I suddenly found myself drafted into the reserve for the first time. It is important for me to note that service in the Israel Defense Forces on a regular basis and in the reserve has helped me over the years to become who I am while overcoming being extremely hyperactive. During the reserved service, we came across an unusual incident during which I responded with combat that included firing on a bursting vehicle. Also in this event, I realized that I have self-confidence and the ability to function and respond prominently.
The reserve duty was over and I returned to work at an event security company. One day, one of the owners of the Mike’s Place club, who was with me in the army, offered me to come and work for him at the club as a security guard. I accepted the offer because it suited as a student and also because I felt that I knew what to do in a job of this type, I felt that I would be able to fulfill my responsibility.
Have you taken a course or professional training for a security guard position?
Avi Tabib: Until the attack on Mike’s Place, I did not take any courses or professional training for the position of a security guard. I learned on my own, on the job, as they say, using everything I went through in military service, combat skills, and working in the United States. I knew and felt that precisely because I was hyperactive I had a professional and clear advantage in the field.
How did you know what to do during the shift?
Avi Tabib: I am an example of how everything a person goes through over the years and his natural nature becomes equivalent to a course, a course from the field, a course of real life.
In time, I realized and believed that readiness meets the opportunity – if you make sure you work right, you will be able to respond correctly.
At the Mike’s Place club I worked in civilian clothes and not in the classic attire of a security guard, which in retrospect turned out to be a kind of possible mistake – it is possible that if the terrorists had identified me as a security guard at the entrance to the club, they would not have chosen the club as the target. Today I can say that in order to be a security guard, one must undergo appropriate professional training.
As mentioned, even though I did not have professional training for the job, I always felt that when needed I would know what to do, and more than that, I knew I would act in the face of real danger. I turned my activeness into an advantage in the field – I joined the staff at the club, I made myself a part of the place, I was part of the team, I made sure to know the club’s regular customers, I formed working relationships and cooperation with the American embassy security guards who worked next to me, I walked around my post and did not stand in one place, my eyes worked non-stop.
I basically created for myself a security environment of collaborating with anyone who was aware of me being the club security guard, everyone would inform me in real-time about anomalous people. So I added more eyes to the field. I remember more than once people would ask me why I was paranoid and that was my sign that they saw that I was active, very active.
What was on the eve of the attack?
Avi Tabib: I worked on the busy days of the club, Tuesday to Saturday, between the hours of 21: 00-04: 00. I was aware of the period of terrorist attacks that took place in Israel at that time. I did not receive any professional instructions from the police to carry out security at the club. Before the eve of the event, I managed to work at the club for about half a year. April 30, 2003, was a Tuesday, a day when the club is crowded with people, about 300 people are inside and outside the club. Throughout the evening you will hear loud music from bands that have come to the club to play.
I arrived for the shift at 9 pm after studies and after karate practice. At around 22:30 the club was fully occupied and at the height of its activity. As usual, I was active, I performed many actions, I controlled the field, I knew who was familiar and who was new, people were always around me, some of the staff would come to me during the evening to draw my attention to exceptions or just to talk. I have always been able to pay attention in an active and noisy environment so it did not stop me from being focused on the task. The evening progressed, at 00:50, I lift my head above the heads of the people around me and look south. I recognize a man moving from the American embassy towards the club. I immediately thought to myself that this was a problematic person and told myself that I would prevent him from entering the club. I clearly remember that man wearing a long-sleeved shirt and I did not recognize anything unusual about him in his visual appearance. The same person comes up to me at the entrance to the club and stands in front of me. I classified him as a problematic person and not as a terrorist. I was usually worried that people who could cause problems at the club would not get into it.
What did you do the moment he stood in front of you and after you decided not to let him into the club?
Avi Tabib: First I stood at the entrance so he could not pass me and go inside and then I started asking him:
Avi: Yes.
Terrorist: (Response in English) I want to enter.
Avi: Says in English – tonight you can not enter the club.
Terrorist: I want to come in, have a beer.
The more the terrorist insisted the more I realized I was not going to let him into the club. At that point, one of the staff members came to me to talk to me. I told her to wait. At the same time, I saw the terrorist move a few steps back. I must point out, that up to this point the conversation with this exceptional person was not unusual because such incidents happened to me all the time on all shifts. After the terrorist has moved a few steps away from the entrance, I exchange a few words with the worker. The terrorist sees this and thinks I may not be awake so he decides to move quickly to the entrance to try to get in between me and the same worker. I immediately recognized the terrorist’s movement forward, placed both hands on his waist, and began to push him back to keep him away from the entrance. I felt that the terrorist was allowing me to push him without resistance on his part. Suddenly I felt a kind of alertness in his body a kind of what seemed like a slight resistance on his part.
There was indeed action on the part of the terrorist – this was the point where he decided to press the power button of the explosive device that was attached to his back. 2 kg explosive charge, relatively thin, glued to the back under the shirt, a charge without the shrapnel.
What do you remember that happened to you after the explosion?
Avi Tabib: The next time I remember I was seriously injured in the intensive care unit at the hospital. In retrospect, I know that I was lying under one of the tables and that at this point no one approached me. I think I was conscious and trying to call for help. I did not understand why no one heard me and did not come to help me. In retrospect, it became clear to me that my vocal cords had been damaged by the explosion and that is why I did not have a sound.
Anyone who saw my confrontation with the terrorist and saw the loud explosion of the bomb then said that he also saw me flying backward on her own and just did not believe that there was a situation in which I remained alive. Thought I was dead. Lying down on the table and just dead.
At one point, as part of the treatment of the wounded and the evacuation of the dead, they also reached Avi the security guard and discovered that against all odds he had survived the explosion and remained alive. Avi was mortally wounded. Avi was immediately evacuated to the hospital where he underwent complex medical treatment that saved his life. The doctors defined the case of Avi as a medical miracle.
Avi the security guard is transported from the club:

Avi the security guard recovers at the hospital:

Avi was in the hospital for 3 weeks after which he continued the rehabilitation process. In October 2003 he returned to work as a security guard at the Mike’s Place club. In December 2003 he returned to reserve service in the army.
Video describing the event:
https://www.youtube.com/watch?v=3l13BI78UAw&t=5s
What are the lessons and messages from the event and your personal operational experience that you are interested in conveying to security guards today?
Avi Tabib:
The security guard at the edge must first be aware that an emergency can occur during any shift.
A security guard with awareness will be better prepared.
A security guard must believe that preventive actions really work and affect the opponent – visibility, scans, questioning, etc.
An active security guard will be more alert and avoid unnecessary habits in the shift routine.
I learned that being visible as a security guard is very important.
At no stage should the opponent be underestimated.
Many security guards today have no idea what it means to not be alert to a task for even one second – looking at a cell phone, unnecessary calls, thoughts unrelated to work, etc.
Every security guard should know that everyone who looks at him, the security objects, and the opponent, knows if he is doing the security as required.
Avi Tabib is not only the legendary security guard of the Mike’s Place club, but he is also a security guard who already in 2003, long before the field of civil security was regulated with an established mindset and guidelines, managed to define an action based on his being hyperactive, one who cannot stand in one place, a curious person, A suspicious person, an environmentally alert person, a brave person who is not afraid to act and deal with the problem in the field.
For me, Avi Tabib, the security guard from the Mike’s Place club, fits exactly with our professional definition of a hunter security guard – a security guard who believes that his opponent is close and can arrive at any moment:

Avi Tabib is an example of a security guard who is well aware of his strengths and weaknesses and knows how to use them during the task with great wisdom, perseverance, and determination while truly believing time and time again that the opponent can appear at his location, in his shift and every shift. Thanks to this belief, Avi was able to cope with the routine and its effects on the security guard during his hard work. This was not the first time Avi recognized an anomalous person in the sector and decided not to let him into the club, an event of this kind happened to Avi on every shift. The main difference on the eve of the event was that this time that unusual person was a terrorist and not just a “troublemaker”. Until the moment of the explosion, Avi did not know that he was a suicide bomber, which emphasizes the working assumption that every security guard must act constantly to detect anomalies where threats can occur at the moment of identification to carry out an actual security operation appropriate to the existing situation. The security guard is not allowed to clear anomalies based on assumptions on his part, he is obliged to approach and question the person. Avi proved that the actions of the security guard do influence the decisions of the opponent.
Inwardly, Avi Tabib always knew that in the test of truth he would act, he would respond, he would be active, and so it happened that evening on April 30, 2003.
Avi Tabib, the legendary security guard of Mike’s Place, physically stopped a suicide bomber from entering the club and saved from death and injuring dozens of people who were in it that deadly evening. Had he not allowed the suicide bomber to enter the club and activate the explosive device attached to his back, there is no doubt that the number of dead and wounded would have been much greater.
Avi takes every opportunity to lecture the security guards about the incident in order to convey to them what he understood and applied already in 2003 – Avi’s story must become history for every security guard wherever he or she may be.
Remember that security should be maintained with the belief that your opponent is closer than you think!