Article author: Miky Weinberg – Tarantula Technologies Ltd and Octagon Security Ltd Company’s owner.
The attempted assassination of former president and presidential candidate Donald Trump during an election rally in Pennsylvania proved once again that the adversary operates while taking advantage of operational mistakes made by the security system, and in the case in question, the Secret Service is also responsible for Donald Trump’s security. Close protection at the event is a professional sub-discipline that a close protection unit is required to do during the overall mission, therefore it is necessary to present a high operational and professional level to allow the principal to participate in the event as planned and leave it without any damage. The data and facts that emerged from the extensive documentation published after the assassination attempt prove that the Secret Service demonstrated a low level of security at the Pennsylvania election rally event that included professional mistakes that allowed a 20-year-old opponent named Thomas Matthew Crook to shoot at Donald Trump during his speech on the main stage and thus join the long list of assassins in the history of the United States. The assassin managed to fire eight bullets at Donald Trump when one of them grazed his right ear while he turned his head to the right to look at a large sign that displayed data related to the speech. President Donald Trump survived the assassination attempt, the assassin was shot and killed by sniper fire, and the Secret Service found itself once again in a state of failure that could easily be considered a security failure.
Documentation of the assassination attempt:
Secret Service:
The United States Secret Service is an arm of the United States federal government that is part of the United States Department of Homeland Security, and its job is to protect the President of the United States and other people associated with him. The Secret Service also deals with the protection of the White House complex, as well as the prevention of counterfeiting and fraud. The Secret Service operates as part of the US Treasury Department. The operation of the Service began on July 5, 1865. After the assassination of President William McKinley in 1901, the need for a body whose primary function would be to protect the President became clear. Although Secret Service agents have partially guarded the President since 1894, the Service assumed complete protection of the President in 1902. On March 1, 2003, the Secret Service was transferred from the Department of the Treasury to the new Department of Homeland Security as part of the lessons learned after the September 11 attack.
According to a 2012 law, the Secret Service protects:
The White House building and the buildings surrounding it on its sides: the Treasury Department building and the Eisenhower Executive Office.
The president, vice president, president-elect, and vice president-elect.
The immediate members of the presidential family.
Residence of the Vice President and his family. The Vice President and his immediate family.
Foreign diplomatic representatives, foreign heads of state and government visiting the United States, and holders of official positions of the United States abroad.
The presidents’ widows and their children up to 16 or 10 years from the day the children leave the White House.
Former presidents and their wives (unless the wife divorced or remarried) until the day of their death.
Primary candidates for president and vice president.
Specific cabinet members.
Donald Trump’s security at the election rally event:
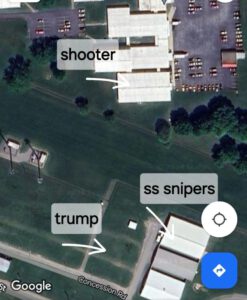
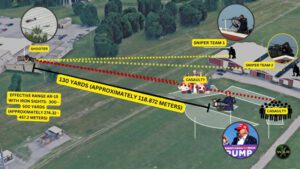
As mentioned, a close protection unit, like the Secret Service, is required to secure the persons under its responsibility during participation in events. Therefore the personnel in the unit, from the level of commanders to the level of individual agents, must know how to plan security at the event. Close protection planning at the event includes gathering data from the protocol, analyzing where the event is taking place, analyzing the relevant threats from the attacker’s perspective, formulating the response to each threat, the security methodology, emergencies, and cases and responses. The phase of analyzing the threats relevant to a specific event is derived from the design of fundamental threats, which, in the case of a single assassin, for example, will determine which firearms he can obtain and at what distance he can shoot with them. From the filmed documentation of the election rally in Pennsylvania, it appears that the Secret Service carried out operational planning that referred to the location of Donald Trump on the stage, the location of the crowd around him, the existence of buildings in the second ring further away, the location of an evacuation vehicle, and more. The area where the event took place was divided into an area for sitting and standing for the audience and an area in the center where Donald Trump stayed; this area included the stage and around it a type of security strip with a pedestrian entrance and exit to and from the stage. According to the testimony of the head of the Secret Service, the third and more distant ring, which was about 150 meters away and included several warehouse buildings, was under the security responsibility of the local police. In 1963, a single assassin with a sniper rifle succeeded in assassinating the current President of the United States, John F. Kennedy, when he fired a precise shot from an office building that was located within shooting distance of the President’s route of travel in the open-air hearse. It was the first time that the Secret Service had to deal with sniper fire and failed and the fourth time that an assassin assassinated the President of the United States. The operational experience of the Secret Service should have resulted in the warehouse buildings in the third ring being its responsibility and not the responsibility of the local police. A threat of sniper fire from a distance of about 150 meters had to be included in the list of relevant threats against Donald Trump. Therefore the event security force of the Secret Service was required to give the appropriate response to this threat. The Secret Service’s decision to transfer responsibility for preventing the danger of sniper fire from the warehouse buildings to the local police is nothing less than a security failure that almost made former president and presidential candidate Donald Trump the fifth president to be assassinated.
Pictures to illustrate the security rings and the distances:

Seeing the attacker – the actions of the assassin Thomas Matthew Crook:
Thomas Matthew Crook, a 20-year-old American who was registered as a member of the Republican Party, may have been the shooter who tried to assassinate Donald Trump so that he could gather information. Crook asked his boss for a day off to do something big. He took his father’s rifle without permission, equipped himself with a laser rangefinder and a scale, and went to the incident area. In the reconstruction that was made, Thomas was first seen about three hours before the event, standing in line for the security check with the laser rangefinder and his cell phone in his possession. The second time, Thomas was seen walking on the lawn a few dozen meters away from the stage. At 5:30 p.m., about 40 minutes before the shooting, he was spotted by the Secret Service, and they circulated a picture of him as a suspect carrying a bag on his back, a laser rangefinder, and looking a bit puzzling. At 17:52, people from the audience saw him climb on the roof of the warehouse with a ladder and start crawling on it to advance to the front line from where he would have a line of sight and shoot at Donald Trump. At 18:02, Donald Trump took the stage and began his speech. At this time, a police officer who heard the crowd’s reports went up with his hands to see if the suspect Crook was on the roof. Thomas noticed the policeman, threatened him with the rifle in his possession, and made him jump down. At 18:11, Thomas started shooting at Donald Trump. In the search for Thomas’ car, explosive devices and a large number of bullets were found, which probably indicates that Crook belongs to those adversaries who left the house with the aim of assassinating a person in a particular event but did not know precisely how they would do it in practice. Crook equipped himself with a relatively large amount of ammunition to have several options for a chosen course of action. From the moment he arrived at the event, about three hours before it began, he began gathering information to decide on the best course of action and the place to implement it. This explains that Thomas only acquired the ladder after he spotted the warehouse within shooting distance with his rifle.
A picture of Crook lying on the roof of the warehouse and a video that records the crowd that recognized him:

The response of the Secret Service against an assassin like Crook, who chose the course of action of firing a long weapon:
As mentioned, the biggest mistake of the Secret Service in planning the event was that it transferred the responsibility for the warehouse buildings in the third ring to the local police – the Secret Service was required to take responsibility for the threat above because of the location of the warehouse and its distance from the area of Donald Trump on stage. Although the security commander at the event placed snipers on rooftops watching over the warehouse buildings in the third ring, including the warehouse from which Crook carried out the shooting, this is considered only a partial response that could not come in place of placing a security force in the area of these warehouses. If the incident security commander had placed security personnel around the warehouse, Crook would also have been monitored during his walk around the warehouse and assured that when he returned to it with a ladder. Additional mistakes in the context of Crook were made when, even though the Secret Service personnel identified him as a suspect, no one approached him to stop and question him about his actions, as well as when people from the audience reported to the police about Crook climbing on the roof of the warehouse. It is not yet clear why, from the moment Thomas was identified as a suspect walking around the area of the event, even before Donald Trump came on stage. Certainly, when he came on stage at 18:02, the commander of the security operation on behalf of the Secret Service did not decide to delay Trump’s entry or take him off the stage to a safe place. Failure to carry out such a decision on the part of the security commander at the event is the one that, among other things, allowed Crook to realize his chosen course of action – shooting Donald Trump from the roof of the warehouse. The sniper fire that hit and killed Crook was too slow and too slow because it did not prevent the shooting at Donald Trump. The failure of the Secret Service to respond to the threat of shooting from a sniping distance proves once again that in the field of security in general and close protection in particular, when you allow the adversary to reach the point of carrying out the act of harming the object of security, you are already in a state of failure and any action that is taken after that one will only minimize or stop the damage and not prevent it.
The shooting and Donald Trump’s luck:
As mentioned, Crook managed to fire eight bullets in the direction of Donald Trump, when only one of them managed to rub his right ear and cause him a relatively minor injury. Donald Trump personally experienced the fact that the level of security provided by the Secret Service was so low that it put his life in real danger, and therefore he needed the hand of G-d so that shortly before Thomas carried out the shooting, he turned his head to the right to see the giant sign planted on the right from which he wanted to get information for his speech. The luck came from the fact that Crook turned out to be a novice assassin who, on the one hand, was able to reach a good shooting position but on the other hand, demonstrated an inaccurate level of shooting, as a result of which he also hit innocent civilians – one bullet out of 8 reached Donald Trump. The simulations that examined the angle of the shot and the angle of Donald Trump’s head show that if he had looked forward and not turned his head to the right, the bullet would have pierced the back of the head, and the result could have been much worse.
Image and video simulation of the angle of impact on Donald Trump:

The low level of security demonstrated by the Secret Service:
An organization like the Secret Service is expected to demonstrate a much higher level of security over a personality who wears two hats: a former president and a presidential candidate in an active election campaign. The low level of security around Donald Trump at the event was seen from the planning stage of the event to his removal from the car. From looking at the visibility and actions of most security personnel in the event’s security system and the team close to Trump, it seems that the Secret Service is securing him with rookies and not with the varsity team. If it weren’t a real incident, I would quickly think it was another training as part of a close protection course that the Secret Service gives new security guards. First of all, it is essential to note that the protocol in the United States is stronger than the Secret Service, that is responsible for security, so you don’t see agents standing near Trump on the stage, they are not allowed, and perhaps that is also why you don’t see an armored podium instead of the funny podium that was placed on the stage and is in no way related to security. From the moment of the shooting, Trump felt and realized that his right ear had been hit and reacted with personal instinct to lower himself behind the funny podium. After a short time, several agents ran towards the stage to wrap Trump and create a human shield against the continued shooting at him. From this moment on, the decision-making sounded confused, with the emphasis on the decision of when to rescue Trump from the vehicle. Undoubtedly, an armored podium would have allowed the close protection team to remain inside it for as long as they needed until a report was received that the area was clear of opponents. It seems that the vehicle’s rescue through an open and unconcealed axis was carried out before receiving a report of an area clear of adversaries. When they decided to set up Trump to get him to the car, the close protection team enveloped him in a way that looked like some kind of improvisation in the field and not like a practice learned in a close protection course. Trump is a tall person, and to deal with this fact, one of the security guards is seen protecting his head with both palms as if they would be able to prevent the penetration of a 5.56 bullet. One of the agents looks like she can’t find what to do with her sunglasses and just holds them in one hand. Going down the stairs, it is not clear why the operation planning did not ensure that it would be more comfortable for an emergency rescue situation; it also looked like a method invented at that moment. The agent who opened the car door to shorten the time of Trump’s entry into it looks like a football player preparing to absorb the power of the opposing team’s player. It would have been better if he had brought the vehicle closer to the stairs to reduce the distance from the rescue axis. As soon as Trump was put in the car, one of the agents was seen trying to put the gun back in the holster and failed, and the agent with the glasses again did not decide what to do with them.
Photos and a video of the evacuation to the car:



Summary:
In assassination attempts that have taken place in the world, including in the United States and Israel, the adversary acts by the course of action he has chosen while taking a risk that he may be caught before carrying out the act of harming the personality until the completion that he will be killed and without really knowing if the security force around him has located him and is working to stop him. In most assassinations and assassination attempts, the adversary succeeds in acting as a result of professional failures of the security system. It is sometimes difficult to understand and believe how “easy” it was for the adversary in the entire process of implementing his course of action, and this explains why various conspiracy theories emerge. The Secret Service is an old and experienced organization expected to demonstrate a much higher level of security and professionalism. The level of protection for the former president and candidate for the presidency may be low due to an organizational decision. At the election rally in Pennsylvania, the Secret Service could have acted to prevent the realization of a shooting threat from a medium distance with relative ease while demonstrating the high level of professionalism that exists in it. On July 13, 2024, Donald Trump received his life as a gift not thanks to the Secret Service but because of him. I fully hope that the Secret Service will learn from the incident and draw clear lessons on planning close protection at events, not placing a new and unskilled security force in the close protection team, and more.
Remember that close protection should be maintained with high professionalism for every principal!