Last February, we spent several days strolling through the amazing city of Rome, which is full of historical sites that attract thousands of tourists every day. Thousands of tourists begin to reach the entrance area of each site sometime before it opens, creating a large and regular concentration of visitors until the site closes. The tourist sites are different in size and attractiveness in the eyes of the tourists and therefore the number of visitors varies accordingly. This also depends on the relevant season. Not all tourist sites create large crowds of people, but there are sites where there is a particularly large crowd all the time, one of which is the Coliseum.
We also went to visit the Coliseum site and to enter it, we had to go through a screening process which included standing in the line up to the entrance ticket checkpoint and waiting in line up to get one’s person and luggage screened. As someone who is constantly thinking and thinking about security, I looked at the security array at the site to answer the question of how effective it is in the face of possible threats.
Although Europe has undergone a process of understanding in recent years that it is necessary to secure tourist areas in general and popular sites in particular, it can be seen that the approach and method of security employed in some cases are incorrect, thus not providing a quality response against the adversary’s possible modes of attack. An adversary who wants to carry out a spectacular attack will look for a place with a relatively large concentration of persons that allows him or her to cause as many dead and injured casualties as easily as possible, as well as preferring a well-known and popular tourism site that will increase the volume and added value of the attack.
To explain why even though there is a security array in place at the site, the tourists who come to it are in real danger, I will refer to the Coliseum’s website while showing pictures for illustration:
The Coliseum site is located in the center of the city and close to other tourist sites that attract thousands of tourists every day. Thousands of tourists arrive at the Coliseum site almost year-round, from the time of opening until the entrance is closed. During this time, there is a relatively large audience outside the entrance waiting patiently for the line to progress and enter the site to visit it.
Picture of the Coliseum site before the audience arrives:

Pictures with the outside concentration of persons who are waiting to enter – on the west side of the site:

Part of the external concentration of persons in the photo from above:


This audience concentration is located outside the starting point of the existing screening process on the site and does not appear to have security guards and / or police officers around.
Later, in the screening lane, there is another concentration of persons waiting to be screened on a with a metal detector gate and a screening machine:

In the existing situation, the adversary has no reason to look for the audience concentration within the site and therefore does not have to deal with the circle of security guards stationed in the screening lanes which include a metal detector gate and a screening machine. The present method makes the concentration of persons stationary, exposed and easy to hit.
Analysis from the attacker’s perspective:
As previously mentioned, the attacking adversary seeks a convenient audience concentration to create a mass casualty event. The concentration of persons at the Coliseum site meets the needs of the attacking adversary, especially that persons who are concentrated outside the area with the screening lanes. It seems that attackers do not have to go through security to reach the external concentration of persons, so there is no reason why attackers should want to try and reach the light concentration of persons that is within the site.
The attacker has no problem seeing, learning and understanding that a security system exists only at the screening posts located within the site area, at the entrance to the site. It should be noted that to reach the internal concentration of visitors, the adversary only has to go through an usher who checks whether the visitor has a ticket and does not search persons and their luggage.
At the Coliseum, as well as on many other tourist sites, one can see that there are 2 crowds that the adversary can choose from. Most attackers will choose the outside concentration of persons as the target for an attack.
What more does a suicide bomber or a terrorist armed with an automatic rifle need than a large concentration of persons that are exposed without peripheral protection?
I think that any agency that responsible for a tourist site that attracts thousands of tourists that create large concentrations of persons has a duty to operate a professional security system that is equipped with security rings that are defined according to a concept and operating method that is written on the basis of an analysis of the area as well as the characteristics of the site (from an attacker’s viewpoint). This is needed to prepare an effective and appropriate response against a potential adversary and fulfill the responsibility for the safety of all people who came to visit the site.
In Israel, several individual entities operate a security system that acts against the adversary using a method of detecting suspicious behavior and checks only those who are classified as anomalous when all the persons go into the facility/site without stopping. I am a big believer in the method for several reasons:
- This requires the facility’s security plan makers and writers to perform an analysis from the attacker’s viewpoint.
- It requires the security guard to think about the adversaries and be active during the shift.
- This eliminates the situation where a security guard becomes passive only because of the wait that a technological measure, such as a metal detector gate, should tell him or her to further screen a person
- It passes the potential opponent through an entryway that has several security rings to detect anomalies – the adversaries feel that they are being looked for
- The security guards approach more people for questioning
- The security guards’ professional level and confidence rise sharply.
This is how security at a tourism site such as the Coliseum should be like:
- The demarcation boundaries of the site must be defined, which includes all the areas where the presence of an attacker can pose a danger to visitors.
- At the site’s perimeter, the audience should be allowed to stay only in areas that are part of the entry and exit route, and the other areas are defined as closed to visitors and bystanders in order one mandatory entry route.
- A number of security layers must be created for detecting suspicious behavioral anomalies, the first layer is placed at the start of the lane and in any segment that can be used by the adversary to organize before entering the site, the second layer is located in an area where there is a concentration of persons, the third layer is placed at the ticket inspection post, The fourth is placed at the last lane of entry into the site itself and the fifth lane is placed within the site’s area.
- Physical layers must be supported with security cameras operated and viewed in an operational and professional dispatch center capable of detecting abnormalities based on suspicious behavior as seen through the cameras.
- The third and fourth layers need to include a metal detector gate and a screening machine to check any person classified as an anomaly.
- Throughout the entrance route and inside the site’s interior, a warning sign has been posted indicating that the site is secured physically and with an advanced and professional camera system.
If all these principles are met, the potential attacker who decides to arrive to gather intelligence or carry out the attack will be required to follow a predefined path where he / she will see active security guards, causing him / her discomfort even to the level of fear and pressure that will result in involuntary actions that will be interpreted by the security system as suspicious anomalous behavior, thus classifying the potential attacker as an anomaly that requires immediate questioning and physical search of his or her person and items.
The above security method will cause the visitors to flow into the site almost unstoppably, thereby completely or almost eliminating an external concentration of persons and forcing the adversary to seek an audience concentration within the site, but the adversary can’t avoid passing through the screening and defensive layers, so he or she has to deal with them.
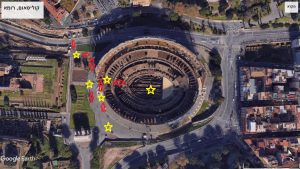
The area of responsibility:

The area for the staging of visitors to enter:

The entry route and location of the security layer:
Remember, security must be maintained while creating defensive security rings that will cause your adversaries to make mistakes!